While hunting for interesting cases, I found the following phishing email mimicking an UPS delivery notification:
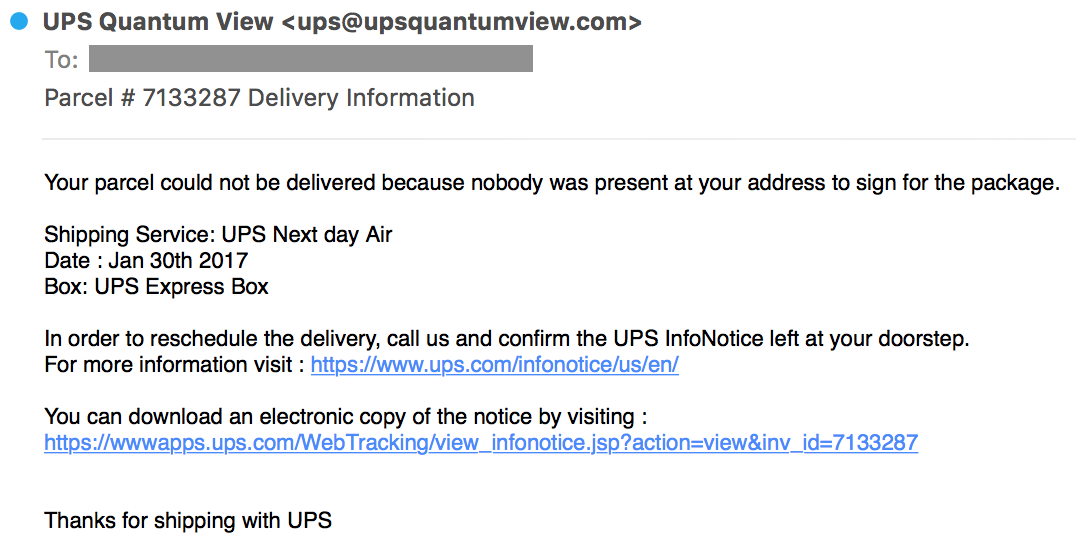
When you click on the link, you are redirected to the following URL:
http://xxxxxxxx/api/get.php?id=zzzzzzzzz
Where zzzzzzzzzz is the Base64 encoded email address of the victim. This link delivers a malicious Microsoft Word file with a macro:
# oledump.py file.tmp 1: 113 \x01CompObj 2: 4096 \x05DocumentSummaryInformation 3: 4096 \x05SummaryInformation 4: 4096 1Table 5: 46803 Data 6: 525 Macros/PROJECT 7: 86 Macros/PROJECTwm 8: M 10403 Macros/VBA/ThisDocument 9: 8458 Macros/VBA/_VBA_PROJECT 10: m 1156 Macros/VBA/blush 11: 839 Macros/VBA/dir 12: M 16661 Macros/VBA/fruitage 13: 97 Macros/blush/\x01CompObj 14: 288 Macros/blush/\x03VBFrame 15: 102 Macros/blush/f 16: 12296 Macros/blush/o 17: 72591 WordDocument
The analysis reveals a malicious file delivering Hancitor[1]. It width:500px" />
It looks that the file visitor.txt contains all the victims who clicked on the link because the file was growing during my investigations. While redacting this diary, the file contains 11587 lines:
The second interesting file is called block.txt and contains IP addresses (1833 lines). It looks to be addresses used by major companies like Google or Amazon. I presume that visitors coming from one of these IP addresses won width:600px" />
Ill now have a deeper look at the list of blocked IP addresses and see if the content could be useful for another diary.
[1] https://www.virustotal.com/en/file/82e3ec80dde9adb2be1c3abe27c37940b3e0ff3b7f2b80b39e10aae540b1fb7a/analysis/
[2] https://isc.sans.edu/forums/diary/HancitorPonyVawtrak+malspam/21919
XavierMertens(@xme)
ISC Handler - Freelance Security Consultant
PGP Key