Wired: Security: Read the Mueller Report; Change Your Instagram Password
SANS Internet Storm Center, InfoCON: green: ISC Stormcast For Friday, April 19th 2019 https://isc.sans.edu/podcastdetail.html?id=6462, (Fri, Apr 19th)
Un informático en el lado del mal: ElevenPaths cumple 6 años: 19 de Abril de 2013. Año 1. Día 1. @elevenpaths @informatica64
 |
| Figura 1: ElevenPaths cumple 6 años: 19 de Abril de 2013. Año 1. Día 1. |
Digamos que, si en un punto dado de tu vida tienes 360 posibilidades para elegir un camino en un plano y muchas más en un mundo esférico, yo suelo elegir aceptablemente bien el cuadrante por el que debo ir, aunque no sepa la dirección exacta, ni mucho menos. Y cuando elijo el cuadrante tiro millas. Rápido. Y después ire aprendiendo y esforzándome al máximo para acercarme a la línea exacta. Pero de momento... al lío.
SANS Internet Storm Center, InfoCON: green: Analyzing UDF Files with Python, (Fri, Apr 19th)
Yesterday, Xavier wrote a diary entry about malicious UDF files.
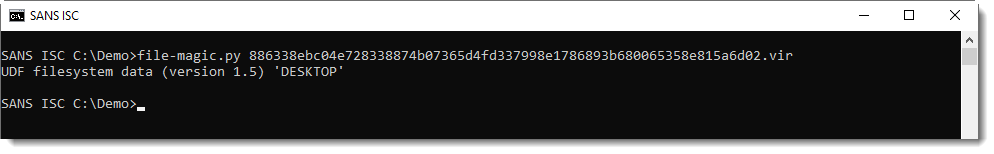
I wrote about the analysis of .ISO files before, and it turns out the same techniques work for UDF files too.
Python module isoparser can also parse UDF files:
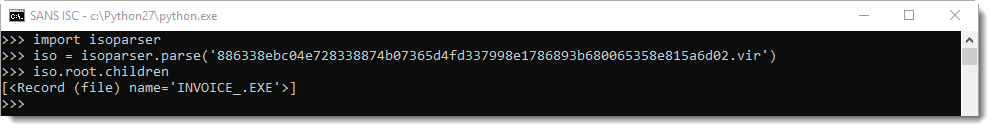
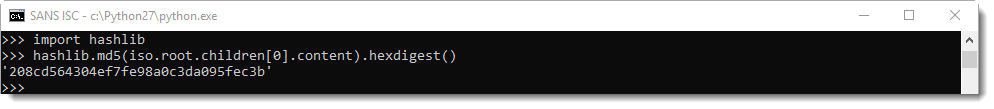
We can retrieve the content:

And calculate the hash of the contained EXE:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.comDidierStevensLabs.com
Didier Stevens: Extracting “Stack Strings” from Shellcode
A couple of years ago, I wrote a Python script to enhance Radare2 listings: the script extract strings from stack frame instructions.
Recently, I combined my tools to achieve the same without a 32-bit disassembler: I extract the strings directly from the binary shellcode.
What I’m looking for is sequences of instructions like this: mov dword [ebp – 0x10], 0x61626364. In 32-bit code, that’s C7 45 followed by one byte (offset operand) and 4 bytes (value operand).
Or: C7 45 10 64 63 62 61. I can write a regular expression for this instruction, and use my tool re-search.py to extract it from the binary shellcode. I want at least 2 consecutive mov … instructions: {2,}.

I’m using option -f because I want to process a binary file (re-search.py expects text files by default).
And I’m using option -x to produce hexadecimal output (to simplify further processing).
I want to get rid of the bytes for the instruction and the offset operand. I do this with sed:

I could convert this back to text with my tool hex-to-bin.py:

But that’s not ideal, because now all characters are merged into a single line.
My tool python-per-line.py gives a better result by processing this hexadecimal input line per line:

Remark that I also use function repr to escape unprintable characters like 00.
This output provides a good overview of all API functions called by this shellcode.
If you take a close look, you’ll notice that the last strings are incomplete: that’s because they are missing one or two characters, and these are put on the stack with another mov instruction for single or double bytes. I can accommodate my regular expression to take these instructions into account:

This is the complete command:
re-search.py -x -f "(?:\xC7\x45.....){2,}(?:(?:\xC6\x45..)|(?:\x66\xC7\x45...))?" shellcode.bin.vir | sed "s/66c745..//g" | sed "s/c[67]45..//g" | python-per-line.py -e "import binascii""repr(binascii.a2b_hex(line))"
BreakingPoint Labs Blog: What is Port Scanning?
Un informático en el lado del mal: Y después de Semana Santa: Eventos, Cursos y Charlas en Madrid, Cartagena de Índias, Málaga, Sevilla y Online. @elevenpaths @luca_d3 @0xWord
 |
| Figura 1: Y después de Semana Santa: Eventos, Cursos y Charlas en Madrid, Cartagena de Índias, Málaga, Sevilla y Online. |
La próxima semana, dentro del programa de formación sobre #ciberseguridad de @MSecureTIC, apoyado por @telefonica_ed, estaremos impartiendo el curso "Introducción a la Seguridad de la Información". Toda la info aquí
...And you will know me by the trail of bits: Announcing the community-oriented osquery fork, osql
For months, Facebook has been heavily refactoring the entire osquery codebase, migrating osquery away from standard development tools like CMake and integrating it with Facebook’s internal tooling. Their intention was to improve code quality, implement additional tests, and move the project to a more modular architecture. In practice, the changes sacrificed support for a number of architectures, operating systems, and a variety of useful developer tools that integrate well only with the standard build system preferred by the open-source C++ community.
Worse still, the project’s new inward focus has greatly delayed the review of community contributions — effectively stalling development of features or fixes for the needs of the community — without a clear end in sight. Lacking a roadmap or predictable release cycle, user confidence in the project has fallen. Enterprises are postponing their planned osquery deployments and searching for alternative solutions.
Many of the most secure organizations in the world have already invested in making osquery the absolute best endpoint management solution for their needs. Being forced to look elsewhere would be a waste of their investment, and leave them relying on less effective alternatives. That is why we are announcing the community-oriented osquery fork: osql.
What are the goals of osql?
With osql, we are committed to restoring the community’s confidence in the osquery project, to making the development process more open and predictable, and to reviewing and accepting community contributions more quickly. Our goal is to restore direct community participation.
An open and transparent development process
In the immediate term, osql will be maintained as a “soft-fork.” We will closely track Facebook’s upstream updates without diverging from the codebase. Plenty of completed work is simply waiting upstream, in Pull Requests. We prepared a workflow through which the osql project can accept Pull Requests that the community deems stable enough to be shipped, but which have been ignored by the upstream maintainers. The community can pick and choose its priorities from those contributions, and incorporate them into the next release of osql.

The osql organization on GitHub will be a hub for community projects
Continuous Integration, Continuous Delivery
We’ve also integrated a much-needed public CI using Azure Pipelines, which will build and run tests at each commit. Find the results here. The CI will help us build, test, and release faster and more frequently. We are committing to release a new osql binary (package installer) on a regular monthly cadence. We will communicate the changes that users can expect in the next release. They will know when to expect it, and that the version they download has passed all tests.

Determine if the latest code is building for all platforms, at a glance
Restoring standard tool support for developers
We rewrote the build system from scratch to return it to CMake, the C++ community’s de-facto standard for building projects. This effort was non-trivial, but we believe it was central to preserving the project’s compatibility with open-source toolchains. The libraries and tools that represent the foundation of modern C++ development, such as Boost or the LLVM/Clang compiler toolchain, all support CMake natively. The most-used third party libraries use CMake as well, making it quite easy to include them in a CMake-based project.
Developers benefit from built-in CMake support in their IDEs. Visual Studio, VS Code, CLion and QtCreator can all easily open a project from its CMakeLists file, enabling a precise view of the project’s structure and the outputs of its build process. They’ll also regain the convenience of CMake-supporting static analyzer frameworks, like Clang’s scan-build, which helps discover critical bugs across an entire project.
By re-centering everything around a CMake build process, we made osql a more developer-friendly project than upstream osquery. If you would like to see for yourself and begin contributing to osql, check out the build guide.

Work conveniently in the Visual Studio Code IDE, with CMake integration
What’s next for osql
Our work is just beginning! We plan to continue improving the automation of osql releases. Initially, osql releases will be unsigned binaries/packages. The next priority for the project is to implement a secure code-signing step into the CI procedure, so that every release is a binary signed by the “osql” organization.
The osquery project’s build process used to allow you to choose whether to download or to build third-party dependencies, thanks to easily modifiable Homebrew formulas. Not only that, you could also choose from where these dependencies were downloaded. That is no longer true for osquery currently, but we will restore that ability in osql (a task made easier thanks to CMake).
We also plan to extend the public CI for osql to enable it to test PRs opened against upstream osquery. This will help the community review those PRs, and provide a kind of quality assurance for their inclusion in a future release of osql.
In the longer term, thanks to CMake’s support for building on various platforms, it will be possible for osql to be built for whatever new systems that the community demands.
Want More? Let’s Talk
When we originally ported osquery to Windows, we didn’t imagine it would become so big, or that it would outgrow what Facebook alone could maintain. A whole community of organizations now deploy and depend on osquery. That’s why we’ve launched osql, the community-oriented osquery fork. If you are part of this community and are interested in porting to other platforms, need special features from the project, or want some customization done to the core, join our osquery/osql support group or contact us!
Wired: Security: Facebook Fails, Russian Hacks, and More Security News This Week
Didier Stevens: Update: translate.py Version 2.5.6
This is just a small update to the man page.
translate_v2_5_6.zip (https)
MD5: 9615167810202129C0CFC3D5125CC354
SHA256: F926E474B966790A1077B76C029F912100128C4F1CE848781C14DF4B628395D7
Un informático en el lado del mal: Unas charlas: Navarra Lan Party sobre Datos, CodeTalk sobre cómo entrenar AI y unos minutos de la charla sobre la lengua
 |
| Figura 1: Unas charlas: Navarra Lan Party sobre Datos, CodeTalk sobre cómo entrenar AI y unos minutos de la charla sobre la lengua |
La primera de las charlas es la que di en la Navarra Lan Party 2018, invitado por el Instituto Cuatro Vientos de Pamplona con el que tengo una estrecha relación desde hace años, fui a firmar unos libros de 0xWord y a dar una charla sobre el mundo de los datos y, en especial, sobre el tema de Cambridge Analytica y cómo los info-leaks de datos puede utilizarse para crear grandes entornos de Big Data que permita cluseterizar bien los objetivos a ser atacados por Fake News.
Este es un tema del que he hablado en otras conferencias, pero no había quedado reflejado en muchas de ellas, así que aproveché que volvía a mi querida Pamplona y que se iba a grabar la charla en un entorno ameno y cercano con estudiantes y amantes de la tecnología para hacerla.
 |
| Figura 4: Charla en la RootedCON 2019 usando una AI para suplantarme en vídeos |
Y la charla la grabaron en vídeo durante esta Semana Santa, y la tienes aquí mismo, subida a Youtube para que no te pierdas nada de cómo sacar provecho a frameworks como OpenAI Gym. Recomendación extra, aprende mucho Python [Python para Pentesters, Hacking con Python] que por aquí lo usamos mucho para estas cosas.
Figura 5: CodeTalk for Developers: Cómo entrenar tu AI con OpenAI Gym
Al final, de lo que se trata es de que las herramientas tecnológicas de generación de textos, interpretación de la lengua, y lo que es más importante, asistentes digitales, e inteligencias artificiales que se creen en el futuro, traten con cariño nuestra lengua. Algo que es importante más, cuando estamos metiendo sentimiento a las AI basados en la interpretación de la lengua.
Ya os dejé este fragmento de un minuto que publiqué en mi Instagram, pero ahora he conseguido esta otra grabación en la que se puede ver - más o menos - la parte que hice en el congreso. Como os digo, solo unos minutos.
Figura 8: Charla de Chema Alonso en el VIII CILE
Y eso es todo, tres charlas para que pases este domingo antes de volver al trabajo el lunes tranquilo y calentito en casa. Yo hoy me voy a terminar mi colección de cromos de fútbol con Mi Hacker, que lo que se empieza... se termina.
Saludos Malignos!
SANS Internet Storm Center, InfoCON: green: ISC Stormcast For Monday, April 22nd 2019 https://isc.sans.edu/podcastdetail.html?id=6464, (Mon, Apr 22nd)
Un informático en el lado del mal: Hacking Fitness vía Garmin Connect [Parte 1 de 2] #Garmin #Fitness
 |
| Figura 1: Hacking Fitness vía Garmin Connect [Parte 1 de 2] |
 |
| Figura 2: Hacking con Buscadores. Google, Bing, Shodan & Robtex |
Como hemos visto anteriormente en el pasado, en plataformas como Endomondo (Róbame, que estoy así de sano y estoy haciendo deporte) o Runtastic (Otra red social de deportistas que publican su ubicación y su estado de salud) , si los usuarios no han tomado las adecuadas protecciones, si la plataforma no ha tomado las suficientes medidas para evitar los info-leaks y si el servicio web no ha configurado correctamente las opciones de información, la privacidad de los usuarios podría verse afectada, y esto es lo que vamos a ver hoy.
 |
| Figura 4: Proyecto de ElevenPaths sobre info-leaks en webs de deportistas |
En el pasado, el ejercito militar americano, tuvo que prohibir el uso de dispositivos y servicios como Strava, porque los datos que subían sus soldados pudo revelar la ubicación de bases secretas, como vimos en el artículo "¿Los datos de Strava delatan a los militares de USA?"
Análisis de Fichero robots.txt en Garmin Connect
Analizamos en la plataforma la existencia del fichero robots.txt utilizado para impedir a los motores de búsqueda la indexación de cierto contenido web. Observamos que no existe, así que la probabilidad de que los motores de búsqueda hayan indexado información web del sitio, como, por ejemplo, datos de las cuentas de los usuarios relacionados con su actividad física es elevada.
 |
| Figura 5: No existe el fichero robots.txt en la web del servicio Garmin Connect |
Ya hemos visto en el pasado que el tener un fichero robots.txt no es una garantía total, y que incluso se podría convertir en una fuga de información en sí mismo, pero bien configurado ayuda a evitar problemas de info-leaks. Y en la web de Garmin Connect no existe.
 |
| Figura 6: Robots.txt en Garmin Connect not found |
Como curiosidad, al realizar la petición del recurso “robots.txt” al nombre de dominio principal, observamos que sí que existe, aunque “de aquella manera”, porque no ha sido configurado siguiendo buenas prácticas. No
 |
| Figura 7: Fichero robots.txt para el nombre del dominio principal |
Además, no es posible obtener información interesante a partir de las rutas relativas de recursos almacenadas en el fichero “robots.txt”. No obstante, hay que recordar que el sitio web podría hacer uso de Headers HTTP X-Robots-Tags "NoIndex" o de etiquetas HTML META NoIndex en páginas web para evitar la indexación, así que la prueba del nueve es comprobar cuántas URLs de perfiles de usuarios de Garmin Connect se han quedado indexadas en los buscadores.
Búsqueda de URLs de actividades deportivas de usuarios
Una vez dentro de la plataforma, en la zona de actividades del usuario, se observa en la URL un posible patrón común para todas las actividades registradas de los usuarios de la plataforma: “modern/activity”
 |
| Figura 8: URL con la información de una ruta en bicicleta de Amador Aparicio (@amadapa) |
Haciendo, como hemos dicho al principio, un poco de “Hacking con Buscadores” se observa como Google tiene indexados casi 100.000 resultados relacionados con la actividad de los usuarios de la plataforma, lo que es una auténtica salvajada. Y desde el punto de vista de negocio de Garmin Connect extraño, ya que está entregando los datos de todos sus usuarios a Google.
 |
| Figura 9: Resultados indexados en Google de usuarios de Garmin Connect |
Con una sencilla consulta, se determina que es posible acceder a la información de las actividades usuarios de la plataforma sin la necesidad de tener una cuenta en ella, seguramente porque la cuenta no cuente con la configuración de privacidad adecuada o porque los usuarios quieran compartir esta información con el resto de usuarios de Internet.
 |
| Figura 10: Información de la actividad deportiva de un usuario junto con el dispositivo Garmin utilizado. |
Además, para cada actividad pública, es posible conocer el dispositivo Garmin que registró y volcó la información deportiva en cada una de las actividades, junto con la versión de software que tenía en ese momento. De nuevo, un info-leak de un dispositivo igual que el sistema de recuperación de contraseñas de Google, lo que permite a una empresa tipo Cambridge Analytica realizar una mejor base de datos de las personas a atacar en campañas de Fake News.
Autor: Amador Aparicio de la Fuente (@amadapa), escritor de libro "Hacking Web Technologies"
******************************************************************************************************
- Hacking Fitness vía Garmin Connect [Parte 1 de 2]
- Hacking Fitness vía Garmin Connect [Parte 2 de 2]
******************************************************************************************************
Dancho Danchev's Blog - Mind Streams of Information Security Knowledge: Flashpoint Intel Official Web Site Serving Malware - An Analysis
SANS Internet Storm Center, InfoCON: green: .rar Files and ACE Exploit CVE-2018-20250, (Mon, Apr 22nd)
Reader Carlos submitted an email with attached RAR file.
In the past, when you received a RAR file as attachment in an unexpected email, it often contained a single malicious Windows executable. For the infection to occur, one would have to open the attachment and double-click the executable.
Nowadays, a RAR file can also be an ACE exploit, like the popular %%cve:2018-20250%%. Infection typically occurs by opening the attachment, and then restarting the computer or performing a logoff/logon cycle.
With oledump.py and plugin plugin_msg.py, one can inspect .msg files:
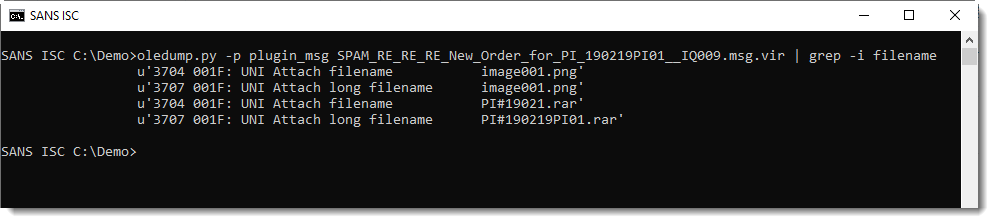
There's an attachment with extension .rar:
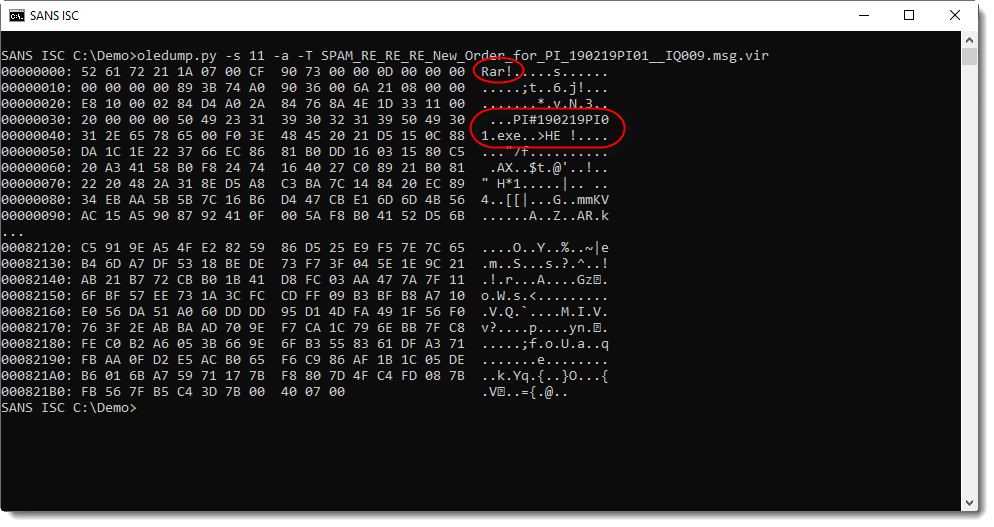
And it is indeed a RAR file containing an executable.
If it would be an ACE file masquerading as a RAR file (.rar extension in stead of .ace), one would see the following:
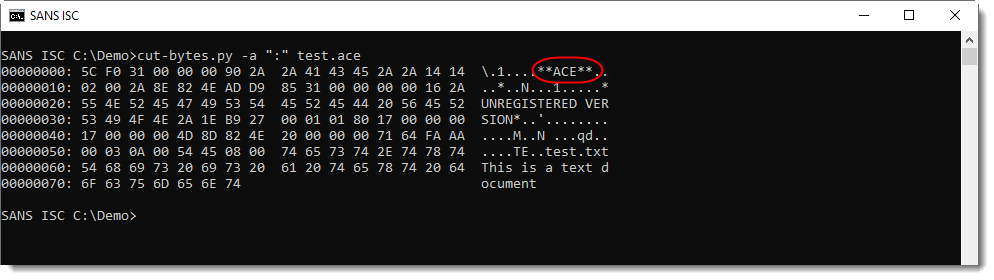
The binary data does not start with "Rar!", instead, one will see "**ACE**" a few bytes into the binary data.
The example above is a normal ACE file. ACE files with a path traversal exploit will have an abnormal path stored in the ACE file:
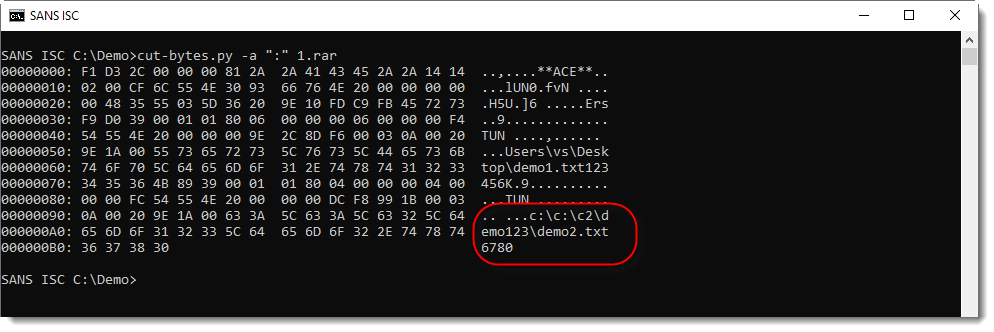
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.comDidierStevensLabs.com
Un informático en el lado del mal: Día del libro en @0xWord Código 10% descuento: DIALIBRO2019 #DiaLibro #DiaDelLibro
 |
| Figura 1: Día del libro en 0xWord Código 10% descuento: DIALIBRO2019 |
El cupón permite conseguir todos nuestros libros con un precio menor de 20 €, y los packs de cinco libros con unos precios en los que el libro sale por unos 15 € más o menos. Una ocasión fundamental para conseguir el material para estudiar, regalar a compañeros en próximos cumpleaños, o disfrutar en forma de pegatinas, cómics o pósters.
SANS Internet Storm Center, InfoCON: green: ISC Stormcast For Tuesday, April 23rd 2019 https://isc.sans.edu/podcastdetail.html?id=6466, (Mon, Apr 22nd)
Wired: Security: A 'Blockchain Bandit' Is Guessing Private Keys and Scoring Millions
SANS Internet Storm Center, InfoCON: green: Finding Local Administrators on a Domain Member Stations, (Wed, Apr 24th)
Now that we've got a list of domain admins ( https://isc.sans.edu/forums/diary/Where+have+all+the+Domain+Admins+gone+Rooting+out+Unwanted+Domain+Administrators/24874 ), lets find all the accounts that have local Administrator rights.
Local Admin used to be a common thing, back in the early XP days when Windows Security was new. It was common back then to see everyone's AD account have local admin on their own machine, so that they could do things like update the clock, install printer drivers, or install games when they took their laptop home.
Sound familiar? Well, those days are gone (or they should be). In 99% of cases, you absolutely, positively do NOT need local admin for anything on a domain member computer (especially if it's not a server) that's administered by IT staff. You might need an extra right here or there, but even then, it's very likely that you don't. Windows 10 and even Windows 7 both do a good job without giving folks admin rights. (We won't talk about that dark Windows 8 detour that nobody took, but W8 does just as good a job on this score)
What local admin does give you is rights that you shouldn't have, to perhaps install malware that might then access system files that nobody wants changed. And if you don't use LAPS, local admin on one station will likely give you local admin on ALL the stations, which from a malware point of view is as good as domain admin in lots of organizations.
So let's get on with it - to find local admins across the board, you'll want something that looks like this:
import-module ActiveDirectory function get-localadmin { $i = 1 |
Note that this code will grab everything, so when it hits the domain controllers it'll enumerate domain admins (which is the honest truth when you think about it). Note also that if a station is not on the network when you run this script, of course you won't be able to enumerate any user information from it.
Run this on your own domain, user our comment form let us know if you find anything unexpected!
===============
Rob VandenBrink
Compugen
SANS Internet Storm Center, InfoCON: green: Where have all the Domain Admins gone? Rooting out Unwanted Domain Administrators, (Wed, Apr 24th)
Ever been in an internal security assessment or penetration test, and need to list all domain admins?
First of all, why would you need to do that? All to often, you'll find that way too many people have domain admins - you know, "just in case"
People like:
- developers - who needed local admin on that one server, that one time, but we gave them domain admin and then forgot
- or developers, because don't all devs need domain admin?
- IT VP's and dev managers, because they used to be admins
- the CEO, because they insisted
- Steve, because Steve needed to update the timezone or install a printer at home, and the helpdesk mistakenly gave Steve domain admin rights for that
You get the idea.
So, aside from the people that are actual members of "Domain Admins", there are lots of groups that have elevated privileges in a domain, so we'll need to enumerate all of those too. And you can put groups into groups, so we'll have to recurse through that mess to get the full list of users. This can take quite a while in the GUI, but it's only a few lines of code in PowerShell:
$DomainAdmins = @()
$a = $()
'Domain Admins', 'Administrators', 'Enterprise Admins', 'Schema Admins', 'Server Operators', 'Backup Operators' | ForEach-Object {
$groupName = $_
$a = Get-ADGroupMember -Identity $_ -Recursive | Get-ADUser | Select-Object Name, samaccountname, @{n='GroupName';e={ $groupName }}
$DomainAdmins += $a
}
$DomainAdmins | export-csv alldomainadmins.csv This will list all the Admin users, and the group membership that put them there. So you might find the same person on this list a few times (but that's a good thing in most cases).
If you just want the de-dup'd list of unique userids (without how they got there), add this snip to your code:
$uniqadmins = ($DomainAdmins | select SamAccountName,name ) | Sort-Object -Property samaccountname -Unique
$pctdomadmins = ($uniqadmins.count / (Get-ADUser -filter * ).count) *100
write-host $pctdomadmins "percent of domain users have domain admin rights"
$pctdomadmins$uniqadmins | export-csv uniqadmins.csv When you run this against your domain, what is your percentage? Did you find any surprises? Please, use our comment form and let us know!
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.